Blog
How to Create an Integrated Security Strategy
By David Crow
In my previous article about integrated security, I explained the fundamentals of a more holistic approach to security. In this article I’d like to share some specific steps in creating an integrated security strategy.
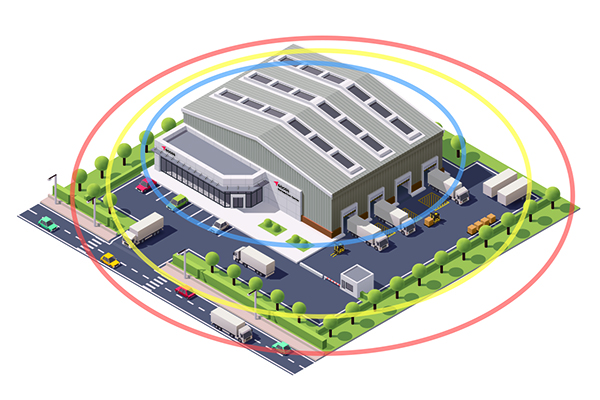
To understand how such strategy works, picture a site as a series of concentric centric circles: The perimeter is the outer circle, the parking lot is the middle circle, and the building is the inner circle.
Without an integrated security approach, the circles are not in constant communication. If someone passes through the perimeter, even an employee entering the site legitimately, how would the teams responsible for the parking lot and building security know about it? With a holistic approach, on the other hand, your security strategy would drive information across each circle of protection, making each circle stronger as we move toward the center.
With new advancements in technology, such as video analytics and remote monitoring, you can enhance your integrated security strategy even further. Adding technology to your security program does not replace a human element but instead augments it. For example, instead of having a whole team on site to patrol a perimeter, you could have a couple of security officers use remote monitoring to secure the site and deploy your on-site employees to other areas of your business.
Creating a Strategy by Working Backwards
 I advise my colleagues to start with integrated security the same way I do with any project: start at the very end. What’s your ultimate goal? What do you want it to look like when you get there? Then ask yourself what you need to make each part work. If you determine what you want it to look like at the end, then you can create steps going backward to build your strategy.
I advise my colleagues to start with integrated security the same way I do with any project: start at the very end. What’s your ultimate goal? What do you want it to look like when you get there? Then ask yourself what you need to make each part work. If you determine what you want it to look like at the end, then you can create steps going backward to build your strategy.
This is especially effective when it comes to budgeting. By working backwards, you can basically pick and choose what fits in your budget this year and then what fits in your budget next year. You might end up with a three-year rollout, but this way you will always have a plan of how to get to the next level and stay within your budget.
Planning backwards also helps you keep sight of your ultimate goal. If you start at the beginning, you could overbuild your security strategy by adding elements you simply don’t need, making it impossible to achieve. If you and your team agree on what you want it to look like at the end, you can make smarter investments in technology and develop strategies that solve the unique concerns of your organization.
Using Integrated Security to Improve Coverage and Reduce Costs
With an integrated security approach, I consider each concentric circle of security and ask myself: “What do we want to get from our security system in this area? What are we trying to understand?”
Let me share an example of how my team and I completely changed how one of our current clients thinks about their physical security. Before we started working together, their typical thought process was, “I put a fence around the property and some cameras, and I’m good to go.” One of their locations contains thousands of vehicles with more than 68 cameras covering the lot and perimeter of the building.
 For one of their new locations we designed a program securing the same total perimeter with just nine cameras. Think of the cost savings of going from 68 cameras to nine. Then after we added thermal imaging cameras, analytics and remote monitoring, this client didn’t need the previous headcount to patrol the entire property, allowing them to deploy their team to other areas of their business.
For one of their new locations we designed a program securing the same total perimeter with just nine cameras. Think of the cost savings of going from 68 cameras to nine. Then after we added thermal imaging cameras, analytics and remote monitoring, this client didn’t need the previous headcount to patrol the entire property, allowing them to deploy their team to other areas of their business.
Next, this client wanted their integrated security strategy to back up their perimeter security and understand the flow of vehicles. So in addition to covering their parking lot with fewer cameras, we also deployed the video analytics that give them the information they needed. Plus, we integrated their gate access control into the camera system to give them better communication across systems.
When we got to the building, we integrated their access control system into the same platform as the camera system to give them more robust reporting of who is coming and going and who has access to where. This reduced costs even further because they didn’t need two different servers to manage two systems.
Before this update, this client also had onsite guards to patrol the perimeter and watch 68 security camera feeds. So we set up remote monitoring with their integrated security platform, which reduced the number of people needed on site while giving the security team better visibility and communication.
With the traditional approach, one may think, “The more cameras the better. I’ll have my security guards look at every security feed.” But the reality is, a guard can only watch one feed at a time. It doesn’t matter how many you put in front of them. So someone could break through the gate, and if the guard isn’t looking at that video feed when it happens, he or she might miss it.
When you add video analytics (software that analyzes what the camera sees), you’ve got that perimeter covered 100 percent because the analytics will alert you about a suspicious event. By adding remote monitoring on top of that, now this client has a whole staff of people who don’t have to watch all nine camera feeds at one time. All they have to watch is when their monitor flashes red so they can pull the feed up and see exactly what’s happening at that time.
An integrated security strategy augmented with technology truly becomes a force multiplier. It gives an organization 100 percent coverage even without 100 percent of the people there.
Partnering with Multidisciplinary Experts
 So you’ve decided to build an integrated security strategy but you’re not sure who to work with. My number-one recommendation is to find someone who understands multiple disciplines, not just individual fields like manned guarding or burglar alarms or CCTV.
So you’ve decided to build an integrated security strategy but you’re not sure who to work with. My number-one recommendation is to find someone who understands multiple disciplines, not just individual fields like manned guarding or burglar alarms or CCTV.
At the risk of sounding like a self-promoter, I’ll share a personal example to illustrate this point. A client I worked with was pleased with their current integrator, who was able to provide them with a camera system that had both digital recording and event monitoring. They also worked with another company to provide manned guarding. But when we sat down and asked them what their goals were and how they wanted to get there, they said, “No one can do that for us.”
“Why not?” I asked.
“Because they’re all different disciplines,” they responded.
When we first met with this client, there were five different buyers at the table, each with a separate responsibility. Over a couple of visits, we showed them that they needed to be able to pull all those niches together into one integrated security strategy. For example, we explained how their cameras work and that they need to be able to send data back to a central system. This system would alert a manned guard about an event, and the guard would then notify another person to block someone’s access.
That’s what a multidisciplinary expert can do for you: They can teach your different solutions providers how to speak each other’s language and show them how to work together.
When we imagine a holistic security approach, we must remember that it’s not just about securing assets. A thorough, well-designed integrated security strategy shows people, both good and bad actors, that you’re paying attention. That’s how you deter bad intent, and prevent theft and trespassing from happening at all. The way you go about building an integrated security program varies based on your operations and the needs of your organization, but the basic ideas stay the same: start with the end-goal, use interconnected systems, and work with technology partners who share the same holistic vision as you.
* * *
 David Crow is the senior vice president of commercial development at Prosegur USA.
David Crow is the senior vice president of commercial development at Prosegur USA.
He is a dedicated practitioner of participatory leadership: leading from within and building teams that are high in engagement, client-focus, results-orientation and camaraderie.
David has over 30 years of security industry experience. Prior to joining Prosegur he held senior leadership roles at SecurAmerica, US Security Associates and The Home Depot.