Assessing your security strategies

In today’s fast-paced world, security has become a necessity for businesses of all sizes. The risks are real, and they’re evolving at an alarming rate. So, the question is: Have you taken a hard look at your security program lately? More importantly, are you aware of its potential vulnerabilities?
Identifying Vulnerabilities: The First Step to Strengthening Security
Every business is unique, and so are its security needs. What works for one organization may not be relevant for another. Conducting a comprehensive risk assessment, tailored to specific operational requirements, can help identify potential risks early and fortify defenses to prevent costly incidents.
What Does a Risk Assessment Involve?
A methodical and thorough approach to risk assessment starts by analyzing current security measures, identifying gaps, and evaluating potential risks that could impact operations. This covers everything from physical security to cybersecurity threats, ensuring all vulnerabilities are addressed.
Global risks, including geopolitical, economic, environmental, and technological factors, are constantly evolving. The geographical environment further shapes and amplifies some of these risks, while digital and physical realms continue to intersect. An in-depth examination of threats at global, regional, and industry-specific levels can reveal key areas of insecurity, allowing for a more strategic security approach.
Areas to Consider
- Physical Security Gaps: Are access points adequately monitored? Is perimeter protection sufficient? Evaluating physical barriers and surveillance systems is essential to ensuring effective protection.
- Technological Vulnerabilities: Is cybersecurity up to date? Are there weaknesses in the network that could be exploited? A deep dive into technological infrastructure can highlight areas for improvement.
- Human Factor: Is the staff well-trained in handling security protocols? Evaluating the human element is vital to identifying where additional training or protocols may be needed.
The Hybrid Security Approach
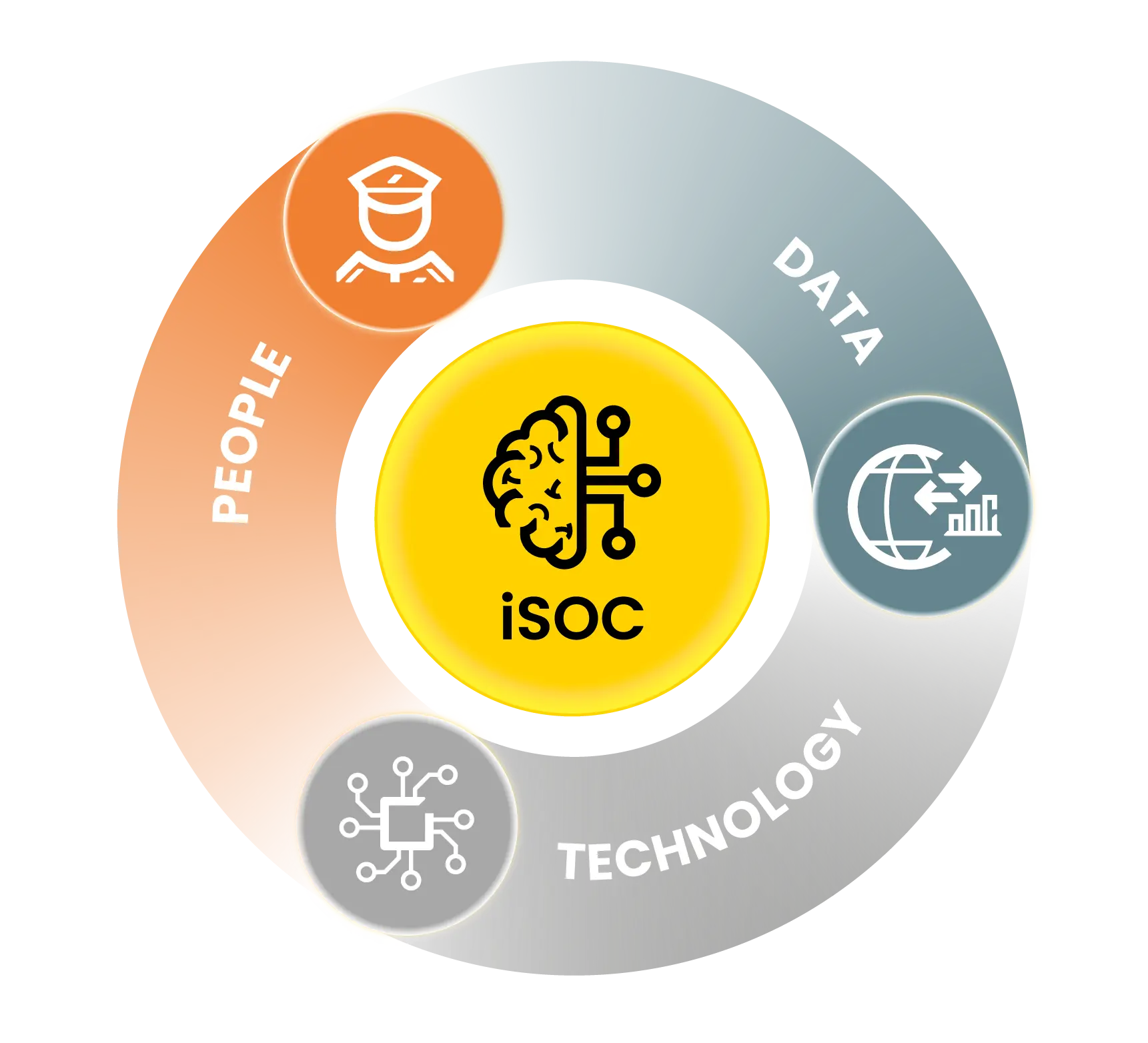
A modern security strategy often involves a blend of human and technological resources. A hybrid model integrates trained professionals with advanced technology, providing a multi-layered solution that enhances overall security measures.
This approach combines on-the-ground personnel skilled in threat detection and response, with AI-driven analytics, remote monitoring, and smart surveillance systems. Strategic data from 24/7 security operations centers allows for quick, informed decisions. Together, these elements ensure that security programs are proactive, not just reactive, with technology enhancing human capabilities for a more formidable presence.
Customizing Solutions for Specific Insecurities
Once vulnerabilities are identified, the next step is developing customized security solutions. Whether it’s upgrading technology, enhancing physical security, or implementing more rigorous training programs, the goal is to build a resilient security program that can adapt to evolving threats.
Conducting a risk assessment offers significant economic benefits by preventing costly incidents, minimizing infrastructure damage, and avoiding legal or regulatory penalties. Identifying and mitigating potential threats allows businesses to operate more efficiently, reducing the need for emergency responses and protecting their reputation. This proactive approach safeguards financial resources and enhances long-term sustainability.
Why Risk Assessments Matter
Comprehensive, multi-layered risk assessments provide insights that allow companies to anticipate and mitigate potential threats before they escalate into significant issues. By understanding the full spectrum of risks—political, economic, social, technological, environmental, and physical—businesses can make informed decisions to enhance resilience and safeguard operations. A tailored methodology ensures recommendations are relevant and actionable, specific to each business’s unique context.
By focusing on vulnerabilities now, businesses can fortify their defenses and create a stronger, more secure future, without waiting for a breach to expose gaps in their security program.
For a full assessment of your facilities, contact our team.
Stay updated with the latest security trends and analyses by following Prosegur's blog.
-
Safety Compliance That Doesn't Annoy Construction Crews
December 4, 2025
-
How to Make Security a Partner in the Patient Experience
November 11, 2025
-
How Safe Buildings Attract and Retain Tenants
November 4, 2025


